SharePoint Sync: Productivity Turned Data Exfiltration
/ 12 min read
Table of Contents
Introduction
SharePoint is effectively a file server and Threat Actors love file servers. Your SharePoint environment is likely a Threat Actor’s dream. In this article, we’ll explore the native sync options that may allow a threat actor to obtain a local copy of your SharePoint site’s contents.
Prefer Video? Watch this on YouTube
What is SharePoint Sync?
SharePoint sync is a productivity-focused feature that allows users to access the contents of a SharePoint site even when they’re offline. This feature is commonly used by people who prefer accessing SharePoint data through File Explorer or who frequently travel. It enables users to remain productive even with limited internet connectivity.
You’re likely familiar with this feature through the OneDrive desktop client, where user OneDrive files are synced to the local device. SharePoint Sync works through the same client yet focuses on SharePoint site content. Once a sync is established, users can work with files directly through File Explorer, with any changes, additions, or deletions reflected both in SharePoint and on the local device. For convenience, Windows 10 includes the OneDrive sync app installed by default.
The Investigation Scenario
Scenario
To investigate the native SharePoint sync options, we can use the following scenario to structure our investigation and testing:
An organisation has identified unauthorised access to an executive’s Microsoft 365 account through a SIEM detection. An initial investigation conducted by their Security Operations Centre identified indications that the Threat Actor had an extended access window of over 60 days. There was no indication that the Threat Actor followed the typical Business Email Compromise playbook with no phishing or payment redirection fraud attempts identified. The organisation extensively uses SharePoint to store information including client-sensitive documents. There is significant concern of the extent of access the Threat Actor had to SharePoint sites in the environment.
Investigation Objectives
The objectives of our investigation and testing include:
- Identify the native methods a Threat Actor can use to synchronise SharePoint Site content.
- Identify controls to prevent unauthorised synchronisation attempts.
- Validate and verify the effectiveness of implemented controls.
We will focus on native sync capabilities within SharePoint. Noting that there are other methods that threat actors may use to exfiltrate data from SharePoint, such as Rclone (if interested check out “Data Exfiltration in M365: Rclone Meets SharePoint” at https://thedfirjournal.com/posts/m365-data-exfiltration-rclone/). For our analysis, we’ll assume the environment is a standard out-of-the-box deployment with minimal configuration changes.
SharePoint Synchronisation
There are two native options available when synching files from SharePoint sites:
- The Sync Button from within a SharePoint Document Library.
- Add a SharePoint Shortcut to OneDrive.
Both options essentially enable the same functionality allowing users to access SharePoint content from within File Explorer. Adding a SharePoint Shortcut to OneDrive is the promoted option to sync SharePoint content; as it allows for content to be accessed on all devices, whereas, a sync is related to a single device.
Sync Button
You’ve probably seen the SharePoint Sync Button before, it is present by default in the options banner within a SharePoint document library. It is very straightforward for a user to sync SharePoint content to their local device through the sync button. To perform a SharePoint sync a user completes the following steps:
- Navigates to the SharePoint document library they wish to sync.
- Selects the sync button.
- The OneDrive desktop application will launch prompting the user to sign-in.
- The user confirms the sync location on their device.
- The sync is established.
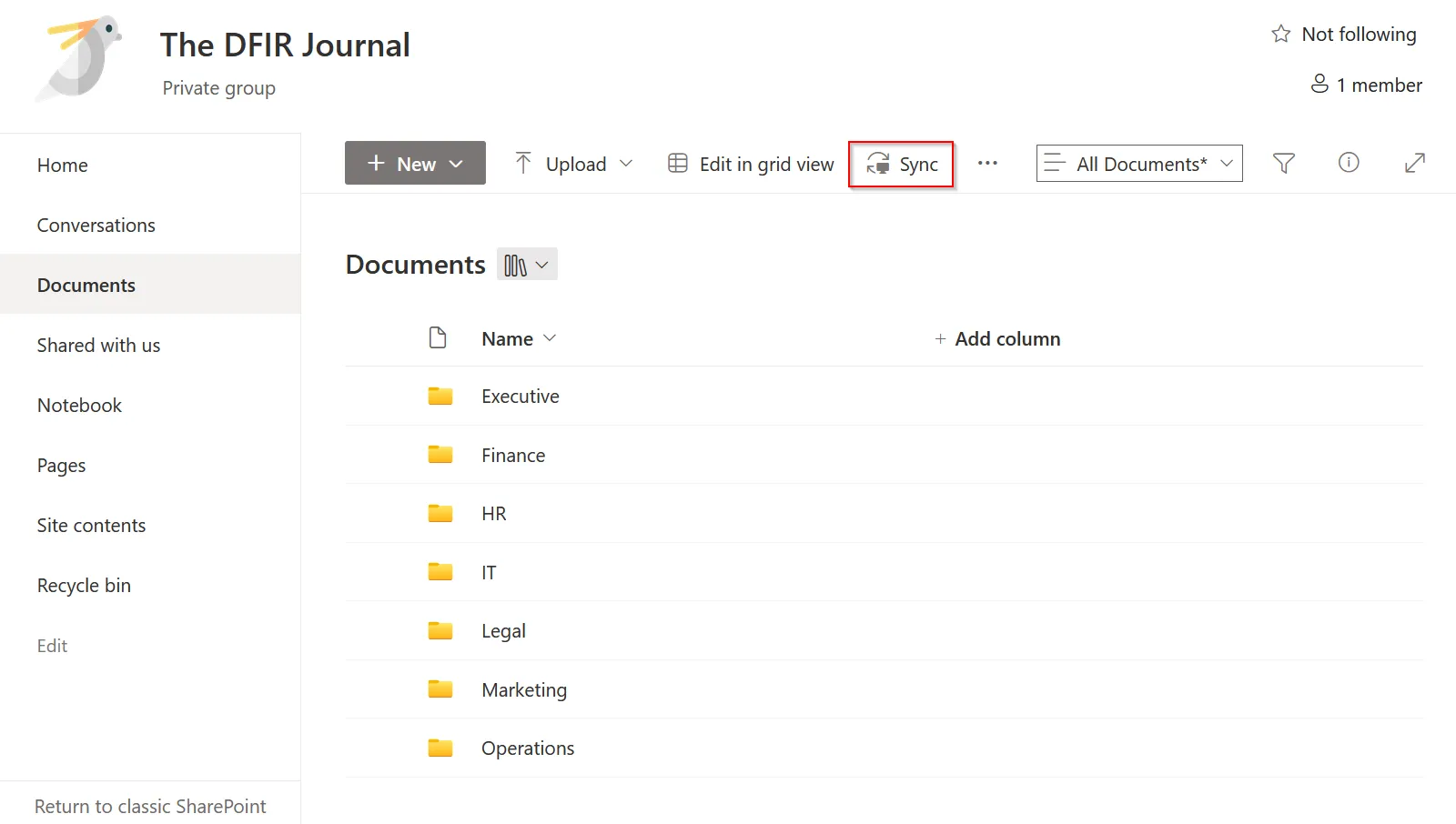
Figure 1: SharePoint Sync Button
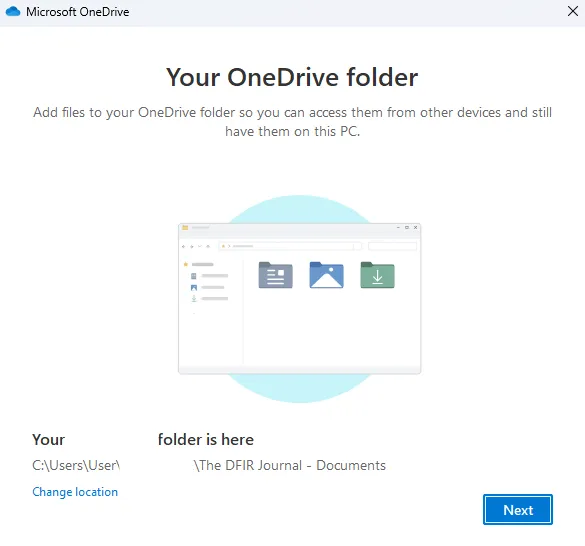
Figure 2: OneDrive Sync Client Local Folder Selection
Whilst a sync is established, this does not mean that the SharePoint site’s content resides on the local device. By default, the sync will leverage a feature known as Files on Demand which adds smarts to the way files are downloaded to the local device rather than downloading all files.
Users have the option to use “Always keep on this device” which triggers and maintains a download of the selected files or folders to the local device. Once this download is complete, a green filled circle appears next to the files, indicating they have been fully downloaded and are available offline.
For more information on Files on Demand check out: https://support.microsoft.com/en-au/office/sync-files-with-onedrive-files-on-demand-62e8d748-7877-420f-b600-24b56562aa70
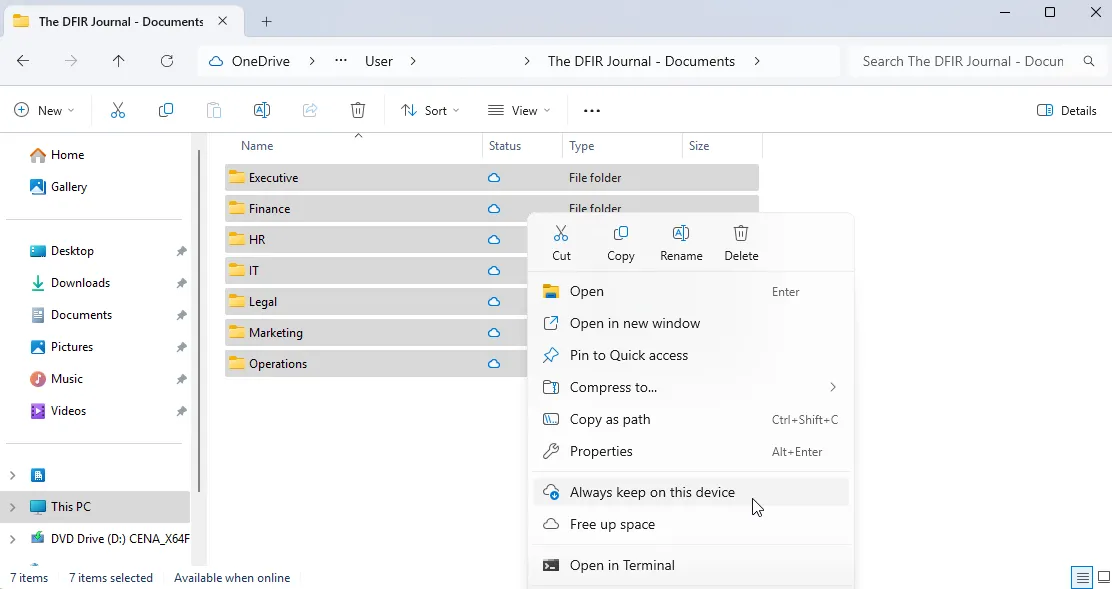
Figure 3: Sync Always Keep on this Device Option
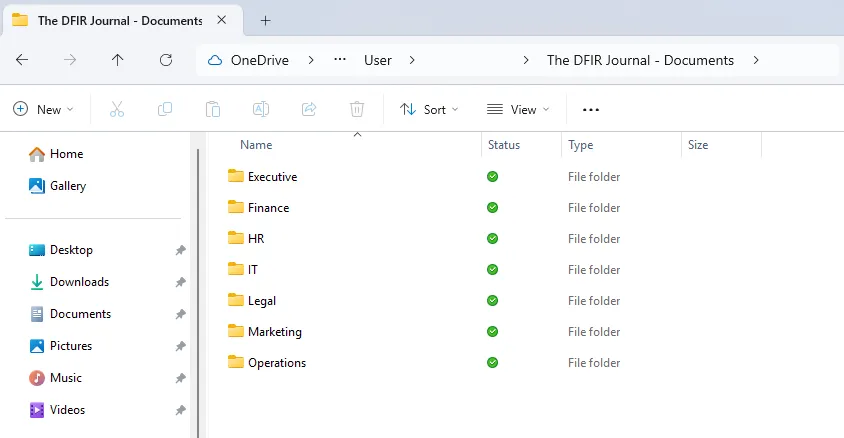
Figure 4: Sync Files Downloaded to the Local Device
Add a SharePoint Shortcut to OneDrive
To create a OneDrive shortcut for a SharePoint document library location a user completes the following steps:
- Navigates to the SharePoint document library they wish to sync.
- Selects add shortcut to OneDrive option.
This will create a Shortcut within the user’s OneDrive which the user can navigate to on their local device and select “always keep on this device” to download the content.
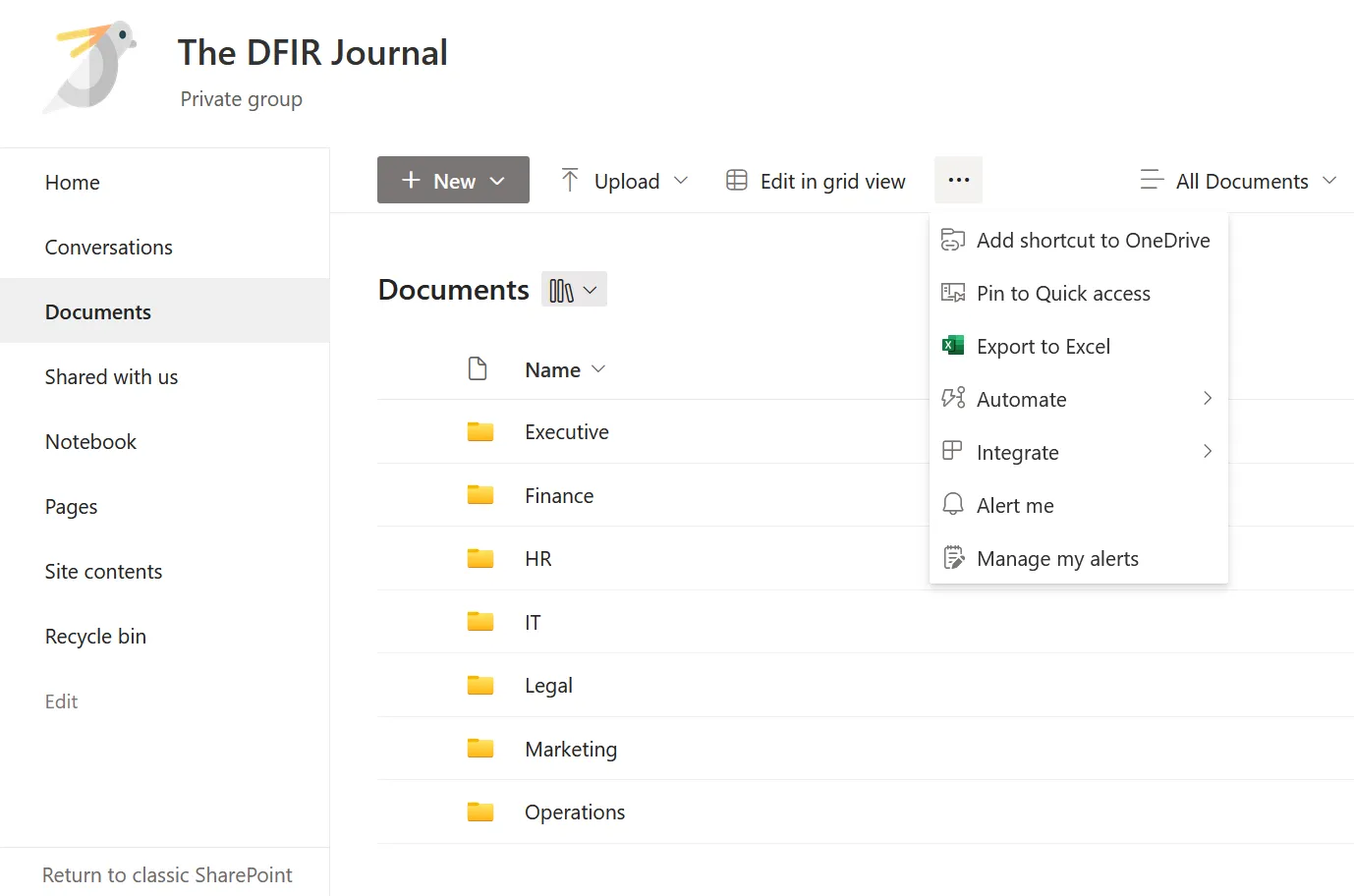
Figure 5: SharePoint Add OneDrive Shortcut Option
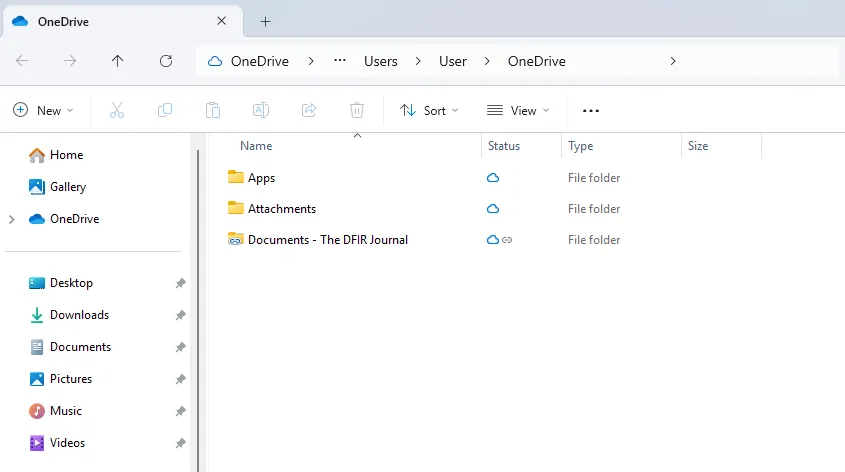
Figure 6: Shortcut Present within File Explorer OneDrive Sync
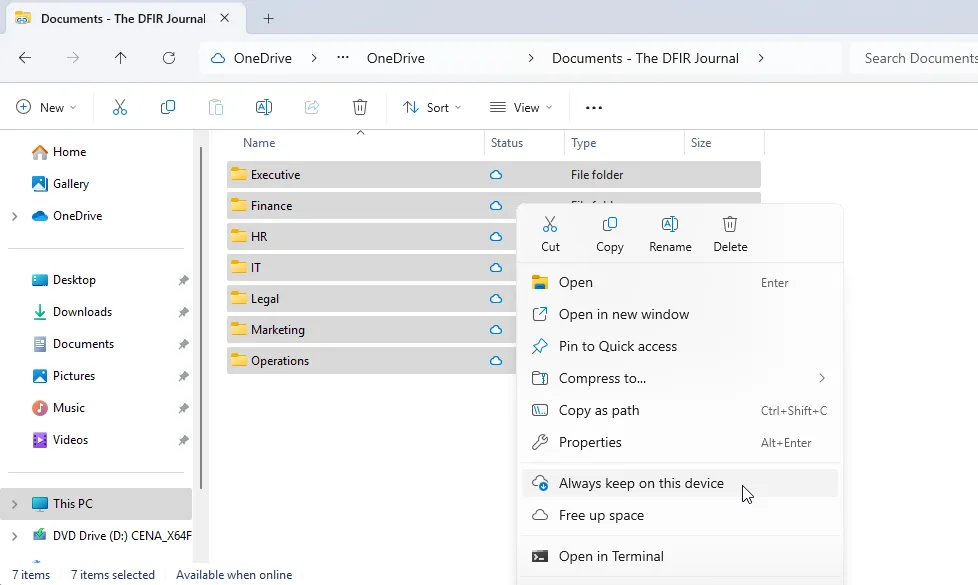
Figure 7: Shortcut Always Keep on this Device Option
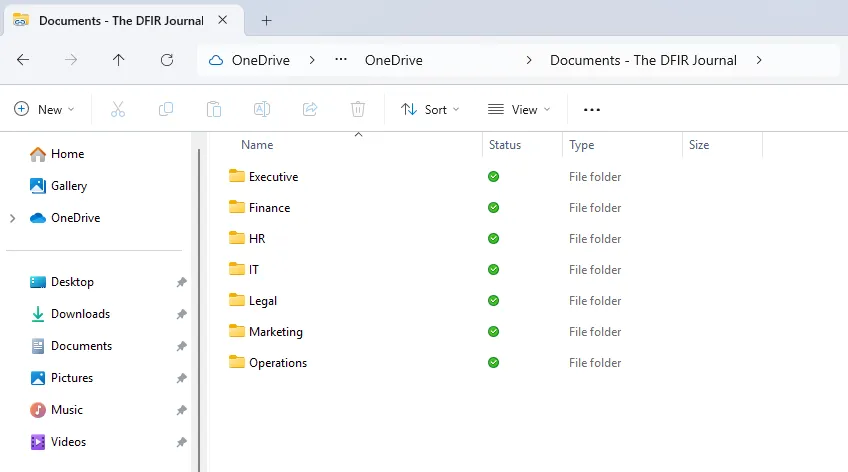
Figure 8: Shortcut Files Downloaded to the Local Device
Where Does This Leave Us
This is pretty concerning considering the opportunities it presents for a Threat Actor. Especially the ease to perfrom data exfiltration from SharePoint where your organisation’s sensitive data likely resides. Where a Threat Actor successfully exfiltrates data on this scale, it could expose the organisation to significant privacy obligations and incident response requirements.
In summary, a Threat Actor who gains access to a M365 account is able to perform a SharePoint site sync and obtain the contents of a SharePoint site. This would result in the SharePoint sites contents residing on the Threat Actors local device and therefore a copy of the SharePoint sites content in the hands of the Threat Actor. The Threat Actor could then leverage this data for a range of motivations such as extortion. Similar in Ransomware attacks when data subsequently is published to a leak site with the goal of a ransom payment.
Forensic Analysis
Let’s explore what is generated from a forensic point of view.
Unified Audit Logs
Unified Audit Logs are the primary log source within M365 containing information on activities performed within the environment, including SharePoint. Following containment, we can collect the Unified Audit Logs for the impacted user. Once parsed we begin to piece together what occurred.
Important
For a sync to occur, a threat actor would need to sign in to the Microsoft OneDrive desktop application. As expected, this is recorded as a sign-in log within the portal and a UserLoggedIn operation within the Unified Audit Log. Within the Unified Audit Log UserLoggedIn operation, this can be identified by filtering on the Application ID field for ab9b8c07-8f02-4f72-87fa-80105867a763 which is the OneDrive SyncEngine Application ID.
The main item of interest is the FileSyncDownloadedFull operation within the Unified Audit Log. This log indicates that a file was downloaded from a SharePoint document library or OneDrive using the OneDrive sync application. This operation is similar to the FileDownload operation which indicates a file was downloaded from a SharePoint site.
The fields within this log are of value to an investigation providing insight into questions such as:
- What content was synchronised? This can be achieved by examining the
ObjectIDsorSourceFileNames. - How much data was synchronised? This can be achieved by summing the FileSizeBytes for all
FileSyncDownloadedFulloperations related to IP addresses attributed to the Threat Actor. - Where was the synchronisation initiated from? This can be achieved by analyzing the
ClientIPandDeviceDetailsfields.
When a Threat Actor performs a sync through the shortcut creation method a ShortcutAdded operation will be present. Of note is the RemoteItemWebUrl field which is the shortcut target document library and the ObjectId field which is the shortcut location.
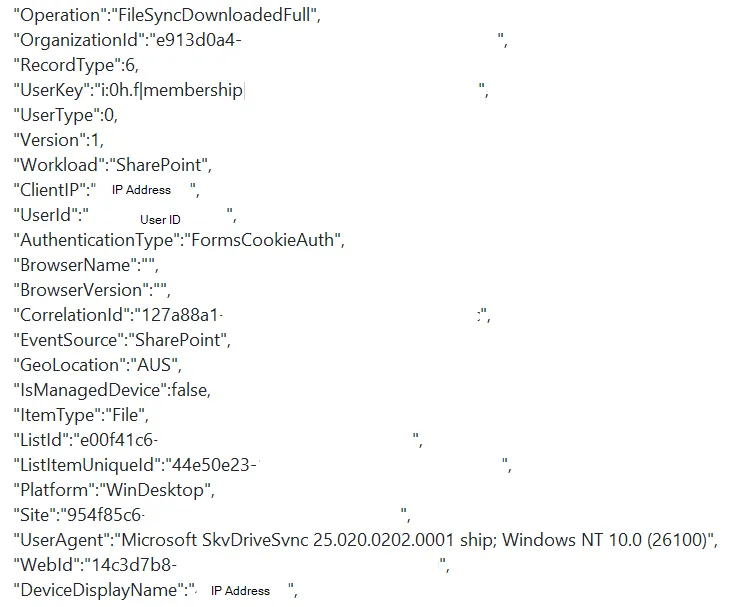
Figure 9: FileSyncDownloadedFull Log Excerpt
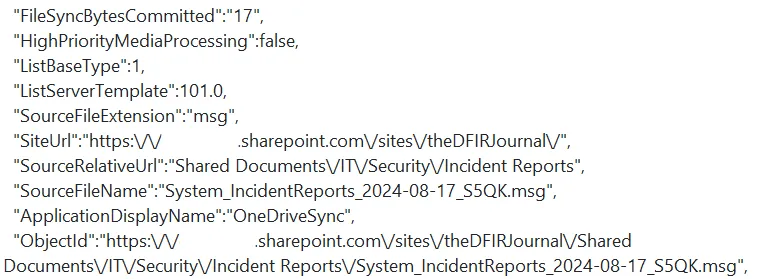
Figure 10: FileSyncDownloadedFull Log Excerpt
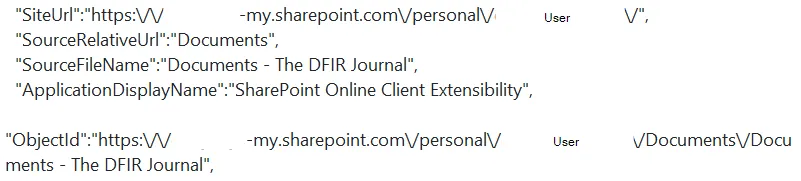
Figure 11: ShortcutAdded Log Excerpt
Detection Opportunity
Prevention
Here are a couple of measures you can implement to prevent this from happening in your environment.
Hide Sync Button
This hides the ease of performing a SharePoint site sync. However, it does not add any controls to actually prevent synchronisation from occurring.
Thankfully, Microsoft warns administrators that hiding the sync button does not prevent users from performing a sync. Prior to writing this article, I was not aware of the sync method through a OneDrive shortcut and discovered it by exploring the prevention methods, thanks to this warning.
Within the Web Portal:
- Navigate to the SharePoint Admin Portal (admin.microsoft.com/sharepoint).
- Select Settings -> Sync
- Within the Sync settings unselect “Show the Sync button on the OneDrive website”.
Through PowerShell:
- Connect to the SharePoint Online Management Shell
- Run:
Set-SPOTenant -HideSyncButtonOnTeamSite $true
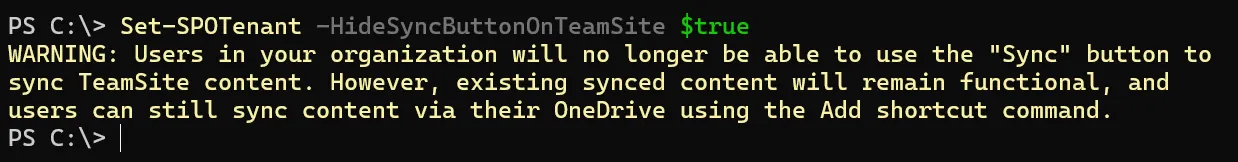
Figure 12: Hide Sync Button PowerShell Warning
Microsoft Documentation: https://learn.microsoft.com/en-us/sharepoint/sharepoint-sync
Offline Client Availability
We can turn synchronisation off all together. This decision depends on your business needs and security requirements. The age old balance between business productivity and security.
Within the Web Portal:
- Navigate to the SharePoint Site.
- Select the setting gear wheel in the top right then select “site information” then select “View all site settings”.
- Within the site settings page select “search and offline availability” under the search heading.
- Change the selection for “allow items from this site to be downloaded to offline clients” to no.
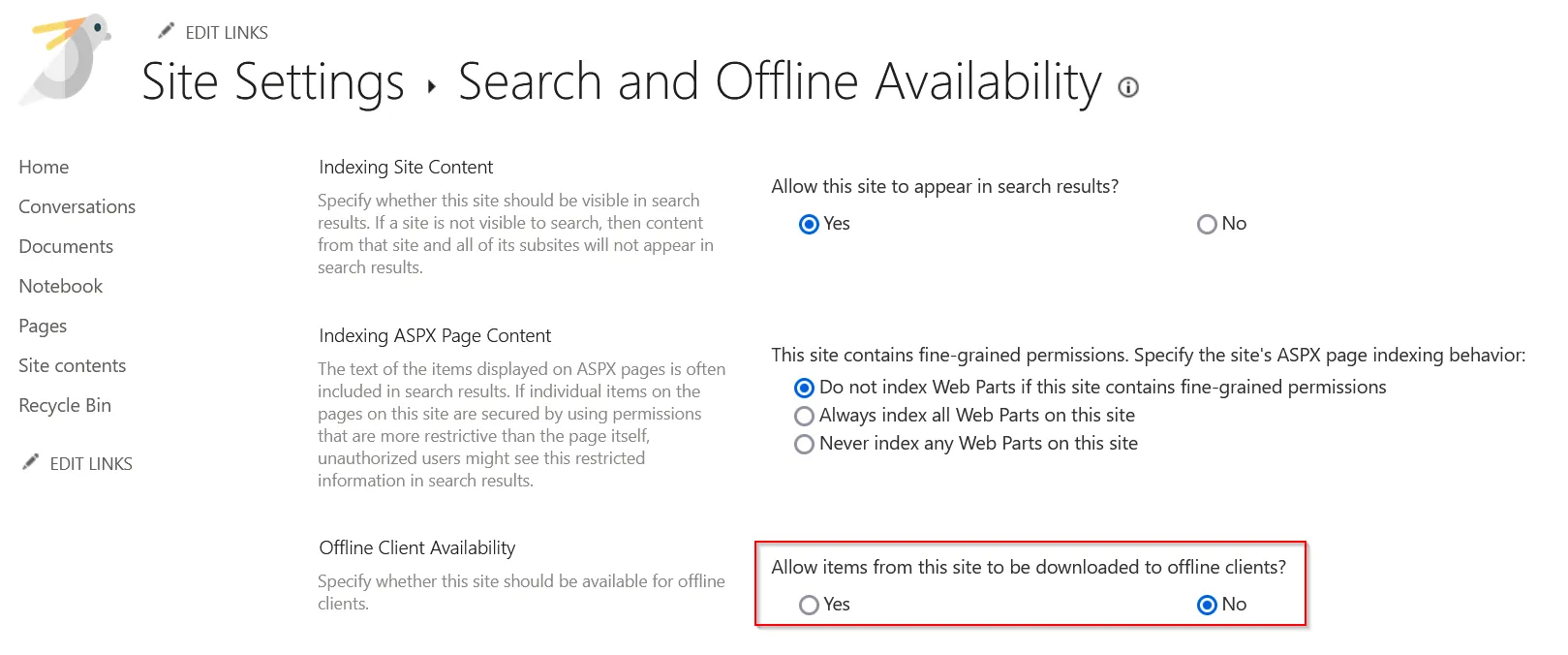
Figure 13: Offline Client Availability Site Settings
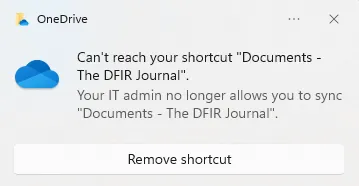
Figure 14: Offline Client Availability Block Notification
Microsoft Documentation: https://support.microsoft.com/en-au/office/limit-sync-for-a-sharepoint-site-e17bf52b-fa5d-41cf-9eb0-d3812542424e
Restrict Synchronisation to Specific Domain
This can be achieved by setting the Active Directory Domain GUIDs within the admin portal. The Active Directory GUID can be obtained with the Get-ADDomain command on a Domain Controller.
Within the Web Portal:
- Obtain your Active Directory Domain GUID/s by running
Get-ADDomainthrough PowerShell on a Domain Controller. - Navigate to the SharePoint Admin Portal (admin.microsoft.com/sharepoint).
- Select Settings -> Sync
- Enable “Allow syncing only on computers joined to specific domains”.
- Enter your Active Directory Domain GUID/s.
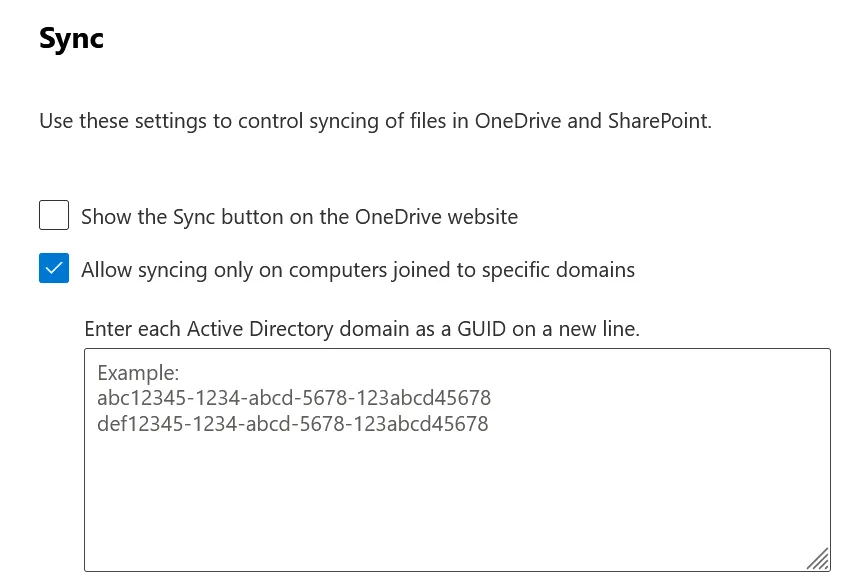
Figure 15: Domain Restriction Site Settings
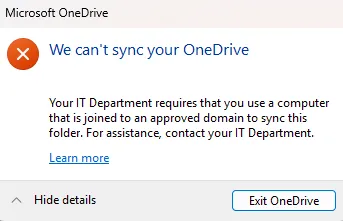
Figure 16: Domain Restriction Block Notification
Microsoft Documentation: https://learn.microsoft.com/en-us/sharepoint/allow-syncing-only-on-specific-domains
Network Location
This is effective but may not support all environments. If you choose this approach, consider restricting to office IP addresses as well as any Virtual Private Network (VPN) addresses. Always ensure Multi-factor Authentication is enabled for all external access.
Within the Web Portal:
- Navigate to the SharePoint Admin Portal (admin.microsoft.com/sharepoint).
- Select Policies -> Access Control -> Network Location
- Enable “Allow access only from specific IP address ranges”.
- Enter permitted IP Address ranges.
Microsoft Documentation: https://learn.microsoft.com/en-us/sharepoint/control-access-based-on-network-location
Block Downloads
Organisations are able to restrict downloads from SharePoint sites. Implementing this control will limit the ability for users to download files from a SharePoint site. Additionally, specific groups can be excluded from this policy.
Microsoft Documenation: https://learn.microsoft.com/en-us/sharepoint/block-download-from-sites
Restrict Access from Unmanaged Devices
This is a great control to prevent access from unmanaged devices which a Threat Actors device would fall under. Note: ensure that users cannot enroll their own devices, which might allow a threat actor to register their device as managed and therefore perform a sync.
Detection Opportunity Operation: UnmanagedSyncClientBlocked
Within the Web Portal:
- Navigate to the SharePoint Admin Portal (admin.microsoft.com/sharepoint).
- Select Policies -> Access Control -> Unmanaged Devices
- Select “Allow limited, web-only access” or “Block access” depending on your risk tolerance.
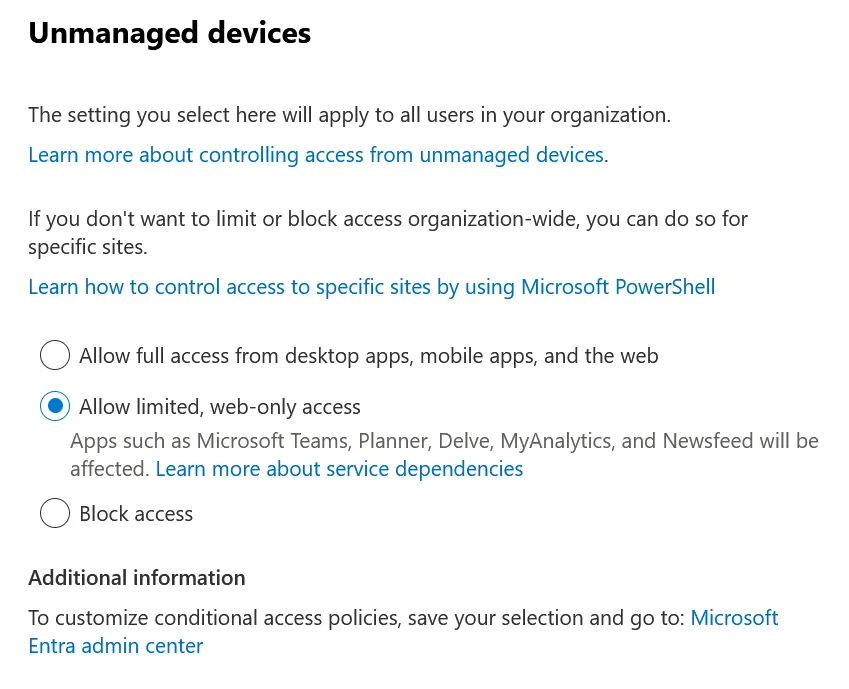
Figure 17: Unmanaged Devices Settings
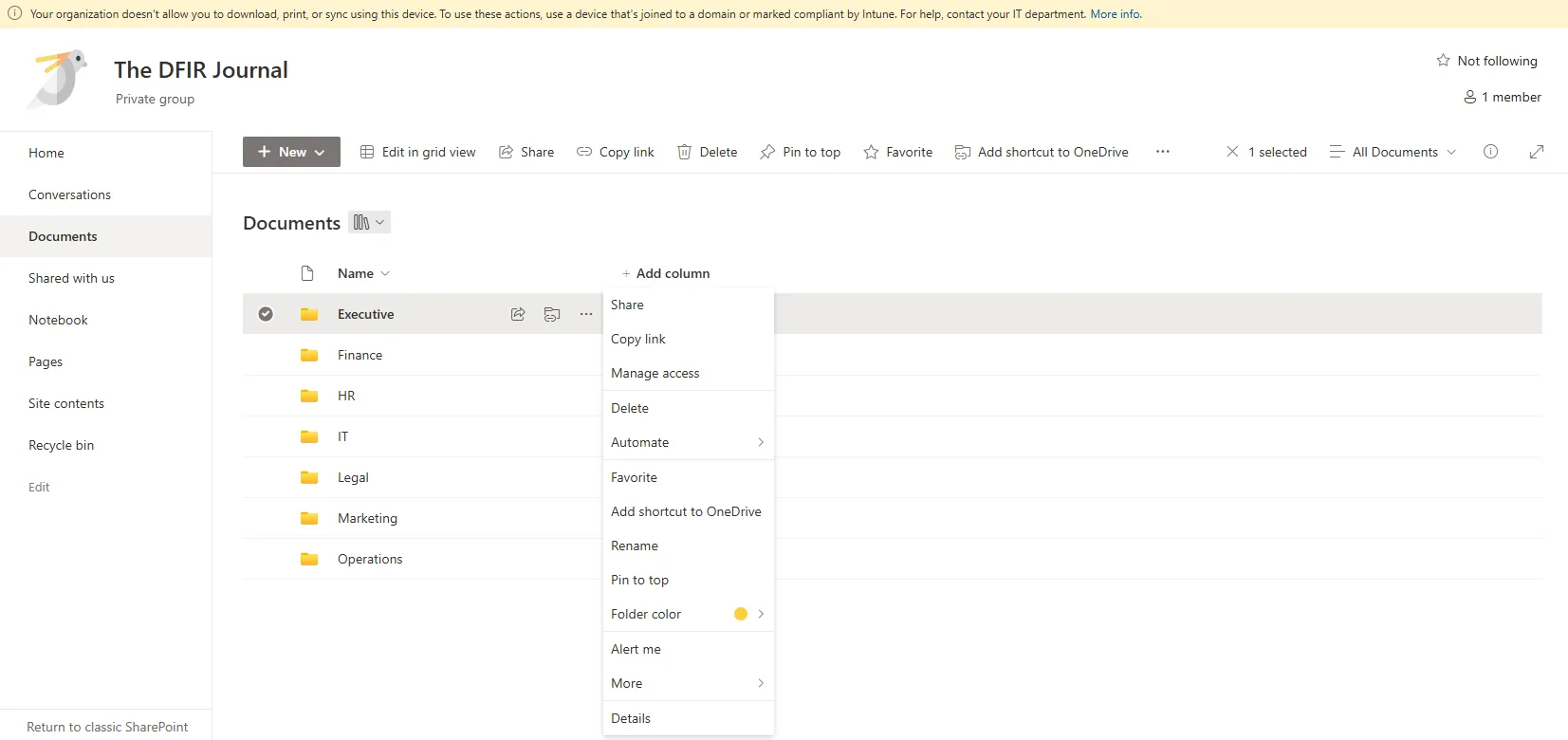
Figure 18: Unmanaged Device Notification Banner
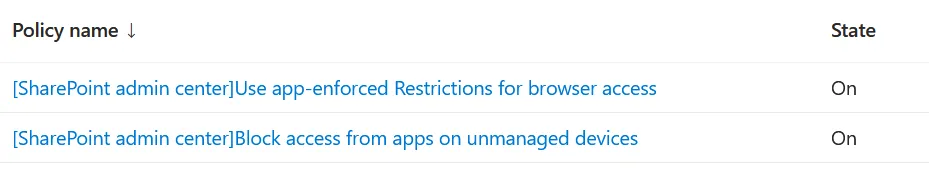
Figure 19: Unmanaged Device Conditional Access Policies
Microsoft Documentation: https://learn.microsoft.com/en-us/sharepoint/control-access-from-unmanaged-devices Further Reading related to Restrict Access from Unmanaged Devices: https://myronhelgering.com/configure-limited-access-for-unmanaged-devices-with-conditional-access/
Final Thoughts
While it is concerning how a feature built to enhance productivity could potentially allow a Threat Actor to obtain a full copy of a SharePoint site, there are several controls available to prevent this from being used in a malicious manner. By highlighting this area of conern, organisations can build detecitons and implement further controls accordingly.
Additional Resources
- How SharePoint and OneDrive safeguard your data in the cloud: https://learn.microsoft.com/en-us/sharepoint/safeguarding-your-data
- Sidestepping SharePoint Security: Two New Techniques to Evade Exfiltration Detection: https://www.varonis.com/blog/sidestepping-detection-while-exfiltrating-sharepoint-data